Veritize™ Verification & Compliance
By Michelle Tan
In the previous articles in this series, we explored why verified data is becoming critical infrastructure—and how Veritize™ captures the physical reality through IoT sensors, QR codes, RFID, and machine telemetry to transform real-world events into trusted data streams.
But captured data alone does not create trust.
Trust is created when data is certified, governed, and enforceable.
This is the role of the Veritize™ Verification & Compliance Engine — the institutional core of Data Wallet™ infrastructure.
Beyond Immutable Records: Certified Truth
Most digital traceability systems stop at immutability.
They record data permanently — but they do not guarantee that what was recorded was true in the first place.
Without verification, an immutable ledger can preserve error, manipulation, or fraud indefinitely.
Veritize™ introduces a pre-ledger verification layer in which every captured event is tested against authorization, provenance, and compliance logic before it is sealed on-chain.
This is the distinction between:
Storing data
and
Certifying truth.
Rule-Based Verification at Institutional Scale
Each real-world event entering the system passes through programmable verification logic, including:
• Facility authorization checks
• Operator credential validation
• Supplier and component provenance
• Process sequence integrity
• Environmental and safety thresholds
• Regulatory compliance mapping
Only when conditions are satisfied does Veritize™ issue a verification signature, allowing the event to be anchored to the blockchain and added to a Data Wallet™ record.
If verification fails, events are flagged, blocked, or escalated for audit review.
Verification is continuous, automatic, and evidence-driven.
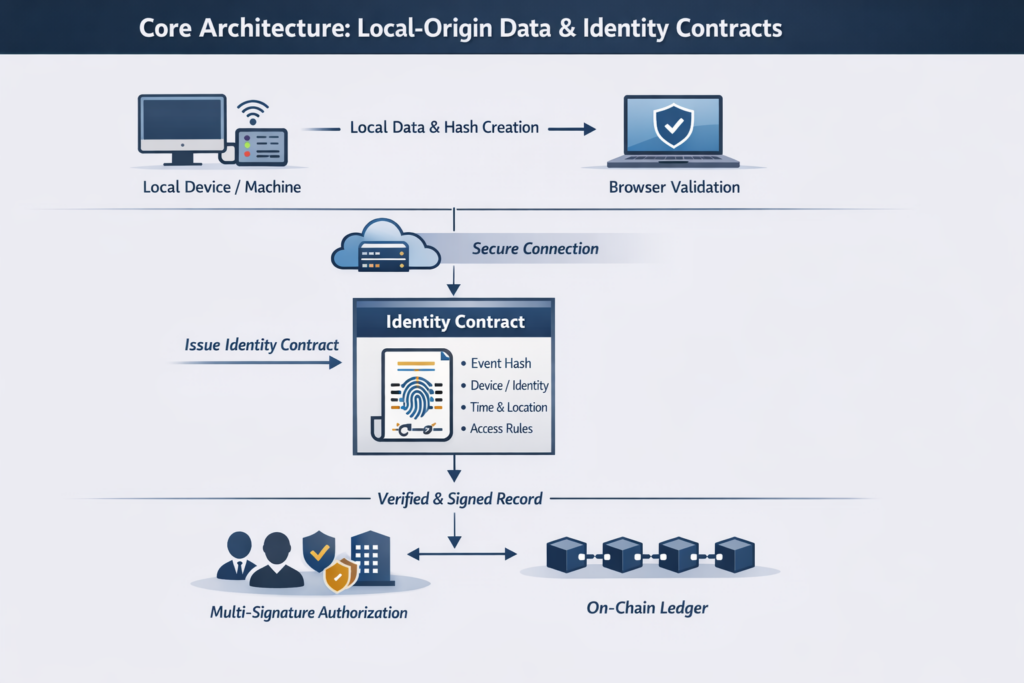
Core Architecture: Local-Origin Data & Identity Contracts
At the heart of Data Wallet™ infrastructure is a critical principle:
Trusted data must be born at the source.
When a real-world event occurs, data is generated directly on the local machine or device where it occurs. The device, browser environment, and verification server establish a secure handshake — ensuring synchronized identity and permission context before any data leaves the source.
The event data is hashed locally, producing a unique cryptographic fingerprint. Because the hash is created before transmission, any later alteration becomes mathematically detectable.
Validation occurs through a browser-based identity interface connected to the verification server. This allows operators, facilities, and authorized systems to confirm identity and permissions in real time — without exposing private keys or sensitive credentials.
Once validated, the system issues an Identity Contract — a smart contract that binds:
• The originating device or operator identity
• The verified event hash
• Time and location context
• Authorization policies governing future access
For high-assurance processes, Veritize™ supports multi-signature authorization, requiring multiple independent parties — such as an operator, facility supervisor, and compliance authority — to co-sign critical events before final ledger anchoring.
Through this architecture:
• Data originates locally
• Integrity is sealed cryptographically
• Identity is verified in-browser
• Authorization is programmable
• Ownership is enforceable on-chain
Truth is not merely recorded.
It is provably authentic at birth.
Continuous Audit and Real-Time Compliance
Traditional compliance relies on periodic inspections and retrospective reporting.
Veritize™ replaces this with continuous cryptographic auditability.
Authorized stakeholders gain access to:
• Real-time compliance dashboards
• Immutable audit trails
• Facility certification histories
• Product-level provenance records
• Automated violation alerts
This transforms compliance from a manual cost center into a real-time operational assurance layer.
For regulators, oversight becomes immediate.
For enterprises, risk is reduced.
For consumers, authenticity is transparent.
A Universal Trust Standard
The Verification & Compliance Engine is designed to scale across industries:
Manufacturing origin verification
Food and pharmaceutical traceability
ESG and sustainability reporting
Environmental asset verification
Intellectual property protection
Real-world asset tokenization
Once verification becomes programmable, trust becomes scalable.

Looking Ahead
With data now captured, verified, and governed, the final question emerges:
How is this certified data owned, shared, and monetized across global markets?
In Next Article, we will explore how Data Wallet™ enables permissioned data exchange, AI-grade data supply, and the foundation of a new data sovereignty economy — where verified truth becomes an ownable and tradable digital asset.
The era of unverifiable claims is ending.
The era of certified truth has begun.

